This article looks at Cryptolocker prevention. My previous article “Cryptolocker is a serious threat to everyone’s data and files” takes a more in depth look at Cryptolocker.
Earlier this week I ran a training session for a client company at their monthly staff meeting to brief them more fully on Cryptolocker and other threats. I also took questions, which they found very useful in helping them to understand what they need to do. The following are some of the highlights from that training session and an examination of some suspect emails.
Last week at Octagon Technology we dealt with another instance of Cryptolocker for one of our clients. A member of their staff had opened a .zip attachment by mistake because he was hurrying through his email. The company was expecting a delivery, which is why he opened the .zip file, but not the package that he delivered by activating Cryptolocker.
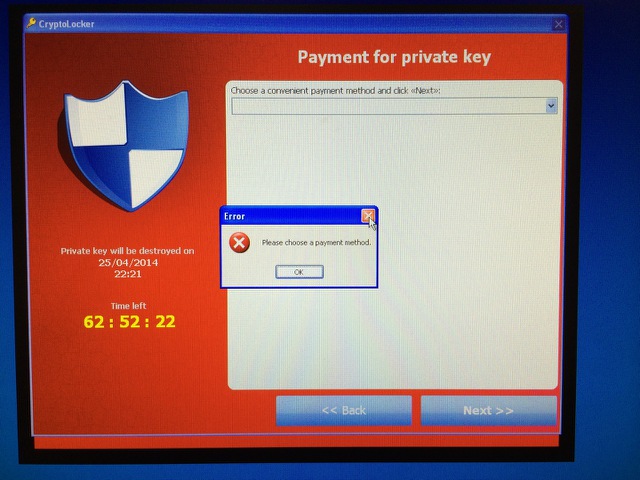
You are infected! If you see this it is too late.
This company’s big advantage in dealing with all their files being irreversibly (unless the ransom is paid) encrypted is that they subscribe to our secure data protection service. A service that:
- is automated
- has multiple days backed up
- has fast recovery times
- is tried and tested
- is monitored and checked – so you can rely on it.
Martin spent the best part of two days onsite helping them recover from this problem. This included:
- removing the encrypted data from the network
- disconnecting and throwing away the infected PC!
- recovering data from a point in the backup earlier than the encryption – and recreating the data store and shares
Unfortunately last week we heard from another IT company that had to help with a company that had not maintained its backup, and had all their files encrypted with no choice but to pay the ransom. In this case paying the ransom (to blackmailers / crooks / extortionists or as one blog I read called them “scum” – you choose) did release their files. But there were some really worried people waiting to see if they got the secret key they needed.
Cryptolocker Prevention – worried?
Cryptolocker Prevention
As email is the most likely way Cryptolocker will get into your organisation and computers, we are often asked about the types of emails people should be suspicious about. Martin has posted several blogs showing examples:
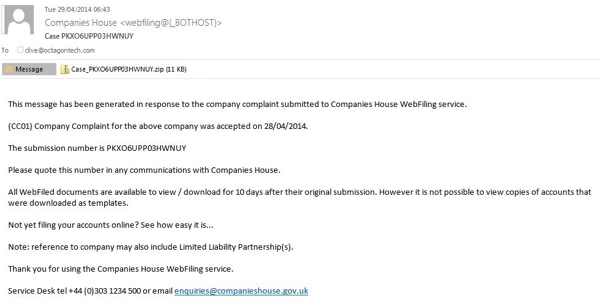
- Companies House Email Warning
- These Virus emails are getting clever!
- More Examples of Cryptolocker Email
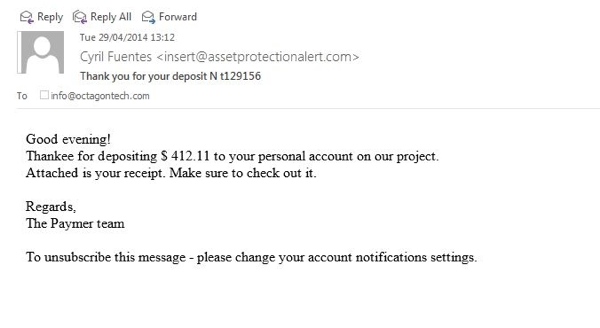
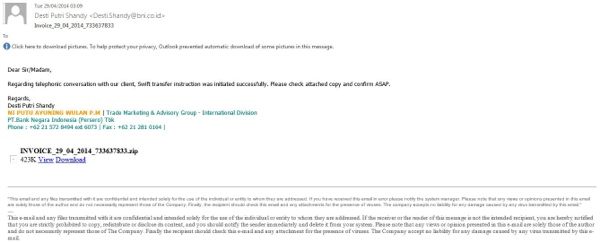
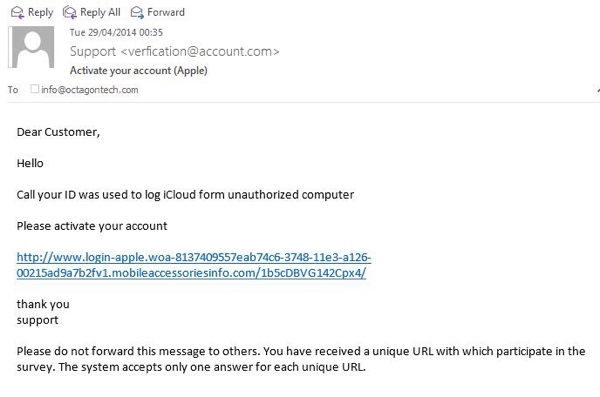
Last night at the Business Club meeting I was again asked about the types of emails that I consider unsolicited and suspect, so today I looked in my email and found five emails that had evaded our spam and junk filtering and the virus protection to make it to my inbox, from where they could pose a threat. (Click on the images below for larger versions if required.)
Our anti-virus software stripped the attachment from the email above. However the grammar and spelling make this email an immediate suspect.
Companies House have a notice here about spam and there is a prominent link on their front page to it.
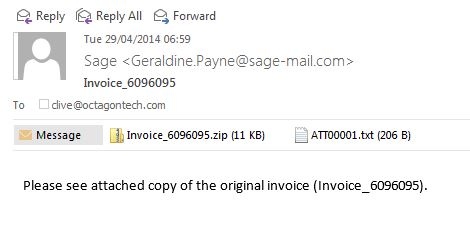
Sage do not have a link from their home page to spam advice – but when I searched for information this page came up.
The email above helpfully suggests I should check all email for viruses.
I have an Apple account but it is not registered to this email address.
Cryptolocker prevention tactics…
- Be really suspicious of unsolicited emails with attachments.
- Delivery companies, banks, health services etc do not communicate with you by email, inviting you to open or look at attached files.
- If the email comes from a source you recognise but you are still suspicious delete it and then phone or email your contact for confirmation they sent it to you – they can always resend it if it is legitimate.
- If in doubt always delete the email – it is better to be safe than sorry…
- Refuse to accept .zip files in your emails – we have.
above is the email signature I use
I hope this article helps you get a better understanding of the threat and I also hope that it stops at least some of you having to suffer the worry of seeing your data lost.
If you would like more advice or help with this issue, protecting your data in a secure offsite environment, or other Trojan or virus issues call me on 07943 537804.
Clive
(c) Octagon Technology 2014