I love technology – although I still do not have a flying car (see here and here) but things are getting closer – US airline set to buy flying electric taxis for airport runs – BBC News. These things aside, we all own a range of gadgets from smart speakers, through laptops to the ever-present smart phone, because we all like technology and this has proved a great benefit to businesses. Instead of businesses having to buy these expensive gadgets for their employees, to leverage the commercial advantage they offer, their employees will go out and buy the latest and greatest with their own money and then (most) are prepared to use these gadgets for the business’s financial gain as their prized gadgets have become such an integral part of their lives.
As a business owner you say “no problem” with this scenario.
For it to work though, a business (including one person companies and micro-businesses) needs a Bring Your Own Device (BYOD) policy. This is a document that lays out the responsibilities and usage policies clearly for both sides. I have read very comprehensive BYOD documents that appear to cover every eventuality but for a consultant’s position are actually impractical, unenforceable and probably have privacy issues that could have the company on the wrong end of a law suit.
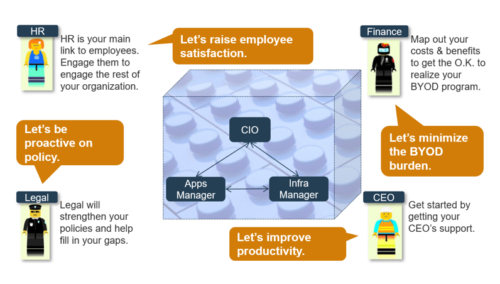
We have some template BYOD policies and for these to be effective in any situation we need to discuss them with the client, understand the relationship between management and their teams and the goals of the business. Then you get the benefits shown in the Lego diagram above.
Remember I said that one-person companies and micro-businesses should have a written BYOD policy – that may seem excessive. However, it can be your safety net when your laptop is stolen, and clients are shouting at you about their data on the machine you have lost and the insurance company is saying the laptop is not covered because you were using a personal device for work. Sounds unreal, but both of these scenarios have happened to people we know.
This is going to be a multi-part series, coming soon:
- Remote Monitoring & Management (RMM) – Big Brother is here but today this is an essential tool for any business
- Protection – anti-virus, anti-malware and web browsing protection
- Work-life balance – an important thing to address
- Back-up everything – remotely, automatically and with retention (back-up archive) the only way to be truly safe
So no conclusion today – you will have to wait for that!
Clive Catton MSc (Cyber Security) – by-line and other articles