Yesterday Martin and I spent best part of the day helping a client who had Cryptolocker on one of their networked PCs – the problem did not develop into a disaster as they are using our secure data protection software.
Below is a document that I have written which is being sent to all our clients to help them avoid Cryptolocker. By also posting it here, I hope it will be helpful for others.
Clive
What is Cryptolocker?
It is a program that when it infects your computer will encrypt your vital files and data, making them inaccessible to you unless you go online and pay a release fee. The following is a list of file types that are attacked – but this list could change at any time.
(source grahamcluley.com)
If your files are encrypted then unless you pay for the key to unlock them, the files will be lost forever.
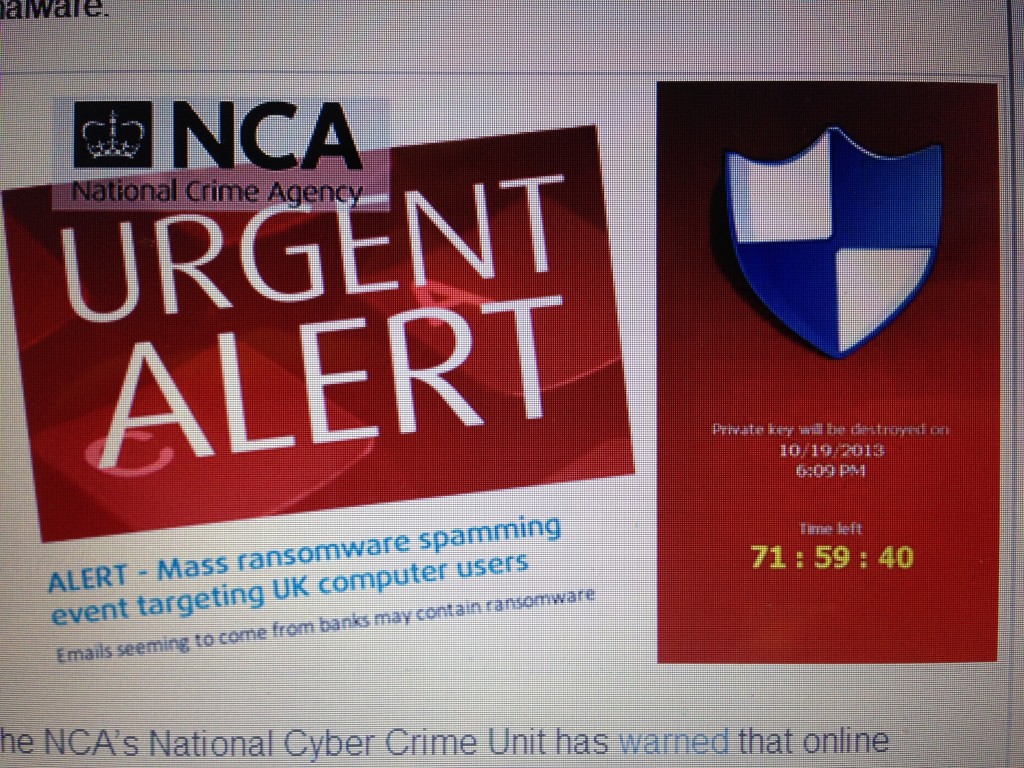
Cryptolocker is this the worst computer virus ever?
The quick answer to this is probably no, but it could be the most devastating malware infection you ever get on your computers. Virus software will remove the problem software but the encrypted files will be gone – unless you pay.
How is Cryptolocker spread?
The primary way this ransomware gets to a computer is in an attachment on an email – the attachment is usually a small .zip file or a PDF file ending .pdf.exe. The best security is not to open any .zip attachment on an email or open a .pdf file from an unexpected source. Unfortunately the latest version of the ransomware is also spreading via infected USB dongles and portable hard drives so extra care must be taken when plugging these devices into your computer. (Your business should put a policy in place about the use of external drives.)
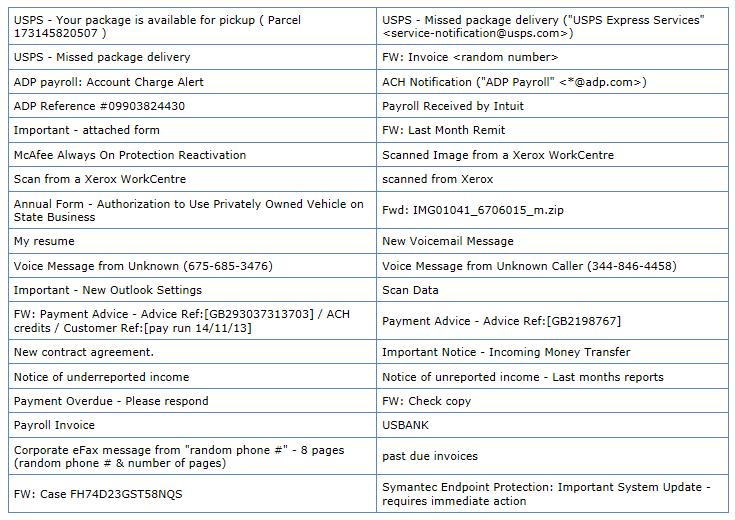
Some examples of Cryptolocker subject lines:
(source bleepingcomputer.com)
What files will Cryptolocker attack?
The ransomware will encrypt any of the files listed above if they are stored in a location accessible from your computer. These will include:
- The local hard drive
- My Documents
- Mapped drives (look in My Computer to see what is mapped on your computer)
- Portable hard drives or memory sticks plugged into the USB ports of your computer
- NAS drives
- Folders shared by users on a network
Cryptolocker will also attack files and data stored online in services such as DropBox or Google Drive if they are shared or synchronised from an infected computer – and then these encrypted files can be passed onto other computers in the share group.
The Best Defence
For peace of mind you will need a backup of your data and files, stored in a location that is not attached to your computer – this excludes online services which synchronise your data rather than back it up.
True online backup solutions are a suitable way to backup your data. Check the retention of your services as the encrypted files will be uploaded to the backup, replacing the good files, which means they could all be replaced before you realise there is a problem. The impact of the only case of Cryptolocker software infection we have dealt with at Octagon so far, was greatly reduced as the company uses our monitored online backup service with a seven day retention plan.
If you backup to a portable device make sure it is unplugged once the backup is finished – however remember that when you next plug it in, your backed up files will be vulnerable to attack.
A longer term archive drive or backup software that produces a file rather than copying the individual files would help to increase the protection offered by any backup solution you use.
Anti-virus and Anti-malware software
Make sure you have reputable anti-virus software installed on your computer, that it is regularly updated and that scans run on your computer at regular intervals. This will alert you to problems but remember that the people who write Cryptolocker (and other viruses, Trojans and ransomware) design their software to avoid detection and they constantly adapt their malware as the Anti-virus companies develop the protection you will be relying on. Hence backing up is the best way to protect yourself.
In Conclusion
This is not meant to be an extensive “how to” document – it is meant to raise people’s awareness of the issues, however here are a few useful resources for those who are more computer literate.
- Microsoft produce good anti-virus software – search Microsoft.com for Security Essentials
- Cryptolocker makes changes to the computer registry – search the registry for “cryptolocker”.
- At Octagon Technology we use Malwarebytes to deal with malware and trojans – malwarebytes.org
- ESET (eset.com) provide a free, well respected tool that can remove Cryptolocker – search for ESET Rogue Application Remover (ERAR) – however remember that if you find you are infected the damage has already been done – get a good backup.
Cryptolocker is a serious threat to everyone’s data and files – everyone should take some simple steps to help themselves:
- Develop a backup policy which is appropriate for your business or personal situation
- Use reputable anti-virus and anti-malware software
- Undertake staff training in the use of email and USB drives
- Keep reminding the people in your organisation that these threats exist
- If in doubt talk to someone who can help you make the decisions that will protect your information, data, files and business.
Clive Catton
Technical Director
Octagon Technology
M: 07943 537 804
Download for free a PDF version of this post – suitable for printing and putting on your office notice board – click here.
To learn more about Ransomware please follow this https://www.comparitech.com/antivirus/guides/how-to-prevent-and-remove-ransomware/