AAA = Authentication, Authorisation and Accountability
AAA is a vital step in any cyber security strategy is:
- Authentication
- Authorisation
- Accountability
AAA, the first two As gives you the ability to control who has access to your information and what information they are able to see. The third A is accountability – without this the first two As are not as effective.
Here at Octagon we need to have access some very sensitive information about clients to be able to deliver to them IT services on which they can rely. To get this service the same clients have to know, without any doubt that we take every step to secure and control access to their information.
We do this by having strictly policies and procedures in place to control where information is kept and how it is used.
To make sure this happens all our team login using multi-factor authentication and once into the system, that identity they logged in with will only allow access to the minimum of information they need to undertake their roles.
For instance our CEO and General Manager do not have access to any of the sensitive information the engineers have access to. There is even some super-sensitive information that only our Operations Manager and myself as CISO have access to. Conversely engineers do not have access to accounting or HR information.
We have a separation of security duties (myself) and admin duties (Operations Manager).
AAA the third A – Accountability.
We may need prove to clients and authorities how we have managed and used our client’s information. For that we use the full range of administration tools available in Microsoft 365 for Business to monitor everyone’s access and use, and the alert system to let us know if there are issues.
What can this do for you?
Below you can see a screen shot of one of our client systems. They had been having some “strange” issues with their accounts and asked us to investigate. On investigation we could see the valid log-in attempts from North London and also more suspect looking attempts from among other places Kathmandu and the Cầu Giấy district in Hanoi, Vietnam! We could reassure the client, from these reports, that these malicious log-ins had not succeeded.
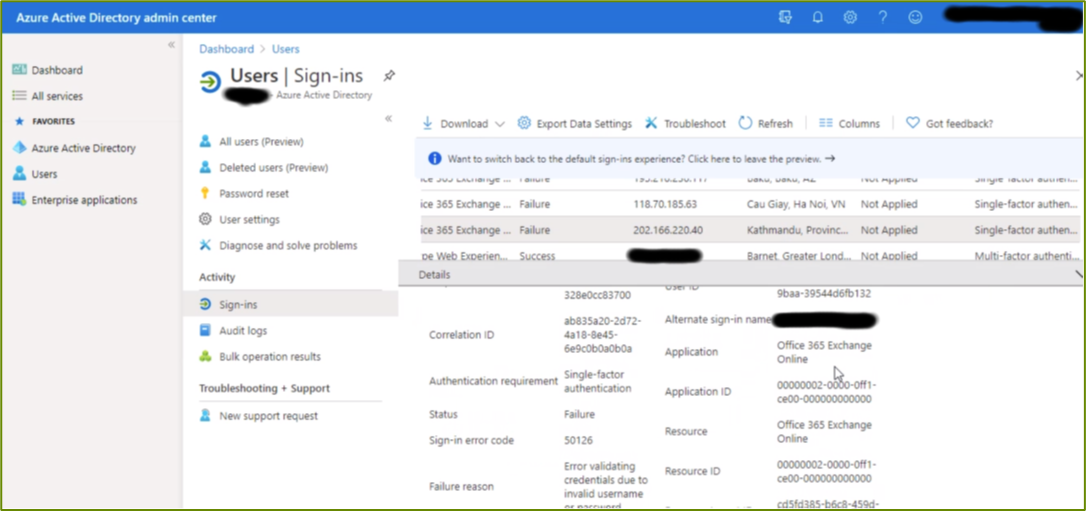
Following discussions with the client, we forced all the valid users to renew their passwords and enforced the use of multi-factor authentication for everyone. We also held an online Q&A training session, for all their people, discussing phishing and social engineering attacks, explaining the new password/MFA policy and other security related issues.
If you think our experience in Microsoft 365 for Business could help your organisation meet its security and compliance responsibilities then you should contact use before that person in Hanoi gets into your systems.
Clive Catton MSc (Cyber Security) – by-line and other articles


