So what does that mean? Click-bait? A riddle? Well, it could be a riddle – it is a quote from Kurt Vonnegut’s 1959 book The Sirens of Titan. If you look these words up in a dictionary most of the words between them are to do with time. Now where am I going with this?
How much spare time do you have? How many things do you have to do and think about when running your business? Lots I am sure, and now I am telling you something else you should be doing when you are already too busy.
This is about using your precious time really effectively to improve your data protection.
Small businesses work hard at delivering their services and products but are poor when it comes to governance and compliance (Berry and Berry (2018) and Bell (2017)). However, governance and compliance are really important and doing them properly will ensure your business runs better and more efficiently in the future.
Below is a table showing a framework for Information Security based on the international COBIT (Control Objectives for Information and Related Technology) system. We use this framework, together with supporting business questionnaires, presentations and workflows to address some or all of these topics for our clients.
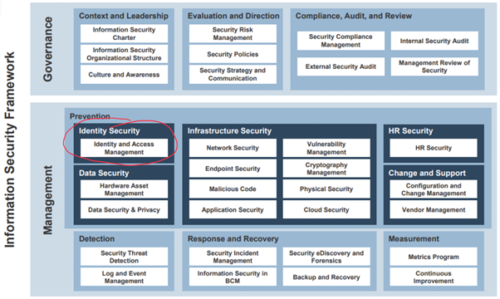
These topics take time to complete but step by step they deliver excellent information security and if you would like to know more about any of the topics get in touch I will be happy to have a meeting with you.
In this blog I address one small part of one topic – Identity Security. If you can keep the bad actors out of your systems you are taking a positive step towards effective information security.
Firstly, turn on and use Multi-Factor Authentication (MFA) for all services and software that offer it – this is a process that authenticates the identity of the person trying to gain access. It is a hugely effective way to improve your data security. Secondly, once your team are using MFA to keep your information secure check they really are – don’t just ask them – check. In Microsoft 365 for Business it is possible to force your users to use MFA and they cannot opt out behind your back.
Thirdly, keep an up-to-date and regularly reviewed record of the systems secured with MFA, actions you have taken to ensure it is used and occasions you have confirmed your team are using it. This is good governance and compliance.
These simple tasks will not take you much time but the return on the time spent is invaluable.
Clive
P.S. For more on MFA here is a link to a presentation I gave giving more details on what MFA does and how to set it up.
References
Bell, S. (2017). Cybersecurity is not just a ‘big business’ issue. Governance Directions, 69(9), 536.
Berry, C. T., & Berry, R. L. (2018). An initial assessment of small business risk management approaches for cyber security threats. International Journal of Business Continuity and Risk Management, 8(1), 1-10.
Information Security Framework source InfoTech Research Group (2021)
If you would like to discuss your information security with Clive, email me at kamila@octagontech.com and I will organise a video meeting for you. He will be happy to answer questions about your particular issues.
Here is a link to the notes for the webinar Clive gave about MFA, as part of Octagon’s Free Friday initiative to share tech knowledge to help small businesses.
Clive has worked at Octagon Technology since 1995. His special responsibility for data privacy and security is a commitment and promise he wants to deliver to his clients. Therefore, to understand these issues better and to keep his knowledge up to date he has recently completed an MSc in Advanced Computer Security and Digital Forensics from Napier University.
It has always been Clive’s ambition to deliver responsive and reliable technology. Therefore, he is always involved in designing, researching and testing technology solutions, particularly where more complex problems exist, to deliver the results their clients need.
To fully use Clive’s new Master’s degree in Computer Security, Clive and Diana have a joint venture with an international research company to get access for our clients to up to date information, schemas, analysis, templates, actionable tools and guidance. Whatever the size of your organisation if you are not approaching IT, security and privacy in a way that supports and benefits you, they can help, from the boardroom to the shop floor.
Kamila

