Yesterday I wrote the opening chapter of this defence-in-depth article – I looked at how anti-virus protection can be side-stepped by threat actors and that staff cyber awareness training is needed to provide another layer to your defences.
That was a human addition to your defence-in-depth and today we are going to look at more technical extra defences.
Cyber Security Threats do not come in just one flavour
The diagram below shows the top five most common cyber security threats – all of which you need to address, depending on your risk.
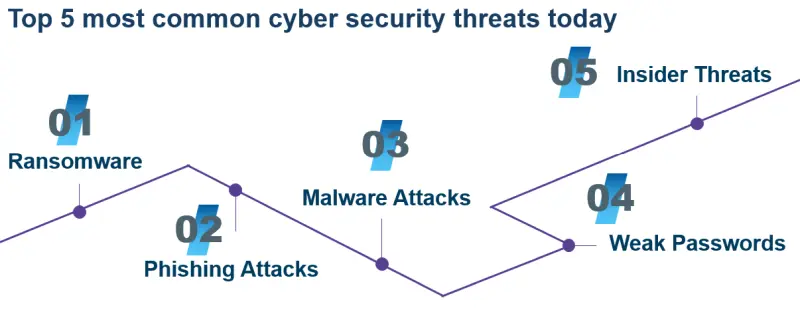
Some of these are addressed by technical defences. Anti-virus software can defend against the ransomware, malware and phishing attacks that are included in the AV software’s current virus definitions – or rather the version of the database that is on your device. But as we looked at yesterday, many phishing emails can sidestep these defences. I also mentioned yesterday how weak anti-virus can compromise these defences.
You can address weak passwords and phishing attacks with cyber security awareness training and a positive security culture can go some way to fixing the insider threat. But to improve your defences you need defence-in-depth.
When you are not looking – logs, logs, logs…
Logs, RMM software and machine learning, when added to a team of experienced cyber security technicians, (all of whom monitor your systems 24/7) is the answer. By taking in information from across your systems and then analysing it and comparing it to the model of your normal operations, indicators of compromise can be spotted and acted upon, even when you (and we) are asleep. This is what our Security Operations Centre does for you.
Not all of these will be an actual problem, maybe someone really is working at 3am, but at least it gets checked out. These systems can spot unknown viruses and ransomware before they appear in the AV databases, as well as the strange actions of an employee or hacker accessing information they should not, and take immediate action to mitigate the attack. They then let us know, limiting the reach of a cyber security incident.
Defence-in-Depth – Are You Interested?
Do you want to take the next step in cyber security with our security stack and Security Operations Centre? It starts at only £10 per head per month and will demonstrate to your team, suppliers, and customers that you really care about your organisation’s cyber security.
Clive Catton MSc (Cyber Security) – by-line and other articles
This article was originally published on Smart Thinking Solutions – our specialist cyber security news blog.
Further Reading
Anti-virus – This is why you need more and better…
Insider Threat – How would you feel if someone betrayed your trust?
Cyber Security Awareness Training
Smart Thinking Solutions | Cybersecurity Starts in the Boardroom
Photo by Tima Miroshnichenko


