Cyber Attacks – What defences do you have?
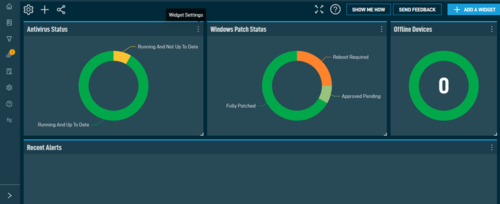
The best strategy for combating cyber attacks, is to adopt automation and 24/7 monitoring. In addition to the comprehensive monitoring capabilities of our software, we employ several other defences to protect against cyber threats. One crucial aspect of our strategy is the adoption of advanced automation techniques. We can swiftly respond to threats and minimise […]
Cyber Attacks – What defences do you have? Read More »