-
Bot Blogging or Blog Botting?

You may have heard of the word processing addon “Grammarly” if you watch a lot of YouTube like myself you will have been subjected to one of their ads by now. It boasts being a ‘must have’ for anyone who writes anything that will be read by anyone else, as well as being able to…
-
Loving My Cycle Tech
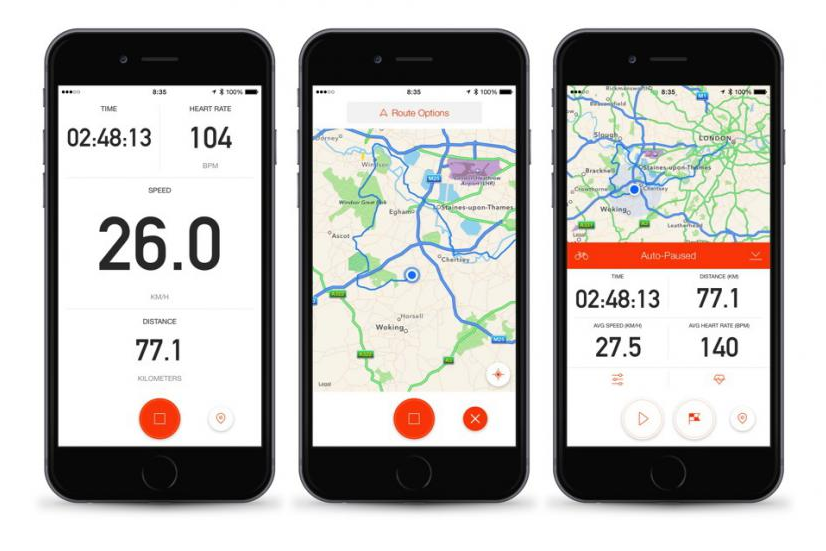
Working in remote tech support means spending a large part of my day sat at a computer. And if truth be told going a little stir-crazy every now and then, especially when I look out the window on a bright sunny day knowing my cycling buddies (the retired and self-employed ones) at that very second…
-
Data Privacy and Security Seminar – the one that you cannot miss this year

It’s almost a year since the General Data Protection Regulation (GDPR) came into effect and we are running a free seminar to help you think about your business data – is it private and secure? This interactive and practical seminar will be run by our CIO Clive Catton who has a special responsibility for data…
-
How to Create a Strong Password

“So I can’t win then, can I? It sounds like you want my passwords to be 25 letters long and look like the cat danced on my keyboard. How on earth do I win?” You ( now frustrated!) Fear not, there is hope. Combine what you have learned and consider the following. Use many words…
-
Factors that impact on a password strength (Section 2)

Any password that is a word, is in the crackers dictionary, and all words of any length can be checked in pretty much the same amount of time when they use what is appropriately called a ‘Dictionary’ attack. This means that all those easy and interesting long words you know, can’t be safely used, at…
-
Factors that impact on a password strength (Section 1)

In our previous blog I introduced three factors that result in a password strength. Here are the first two I mentioned: Factor 1. Number of symbols Symbols here mean any character typically used or usable by the computer, for example numbers consist of ten symbols 0 to 9. Lower case letters a to z are…
-
Ways of stealing your password and top tips to stay safe

There are many ways of stealing a password, but the two main ways traditionally are: Social engineering / Phishing or Vishing Hacking Top tips to stay safe: Number 1) Keep your information private The former requires that you willingly give your information out, perhaps a convincing email claimed they required that information, or a phone…
-
Your password is bad, and you should feel bad – accessibility vs security

Almost all of you will currently be using far too few passwords, most of which are weak. Passwords can be a pain to deal with, they always get in the way and slow you down, there are times when you mis-type one 4 times in a row and you may start to question your sanity.…
-
Data privacy and security seminar

So, you put locks on filling cabinets and rent safety deposit box at your bank? Well done! Your data privacy is important to you. But what about your digital data? Do you keep and share your data in a private and secure way? Are your electronic systems secure? Even a small business will possess the…
-
Do you want snooping with that latte?

Advice for businesses that are out and about, but advice that is just as useful for your personal life and family as well. By now everyone should know that using a public Wi-Fi hot spot is a risk to your privacy and security and when using such connections to the internet you should always use…
-
Fishing Season is Out but Vishing Season is in
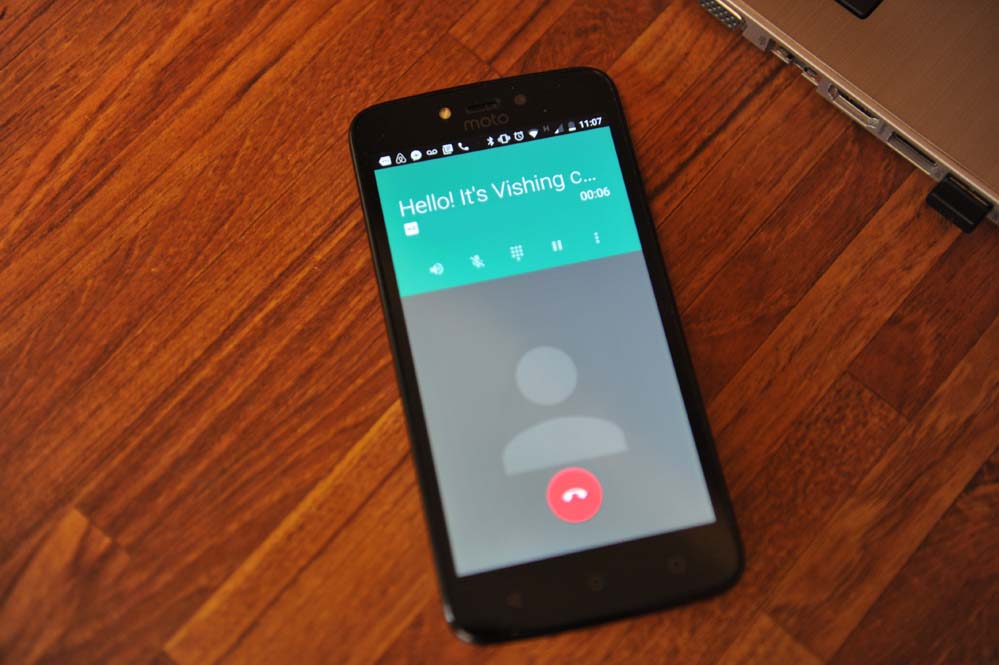
We’ve all heard of phishing, and you may know that it is the reason for most data breaches, as much as 70% Scammers are constantly updating their tactics, and with email scams quite easy to avoid with scepticism, and email scanning antivirus software such as ESET NOD32 Antivirus, scammers are now utilising VOIP technology. Phone…
-
Microsoft OneNote is changing

Anyone who has attended an Octagon Technology presentation, where I have spoken; worked with me in recent years or seen me at a networking event, can not have failed to notice that I love Microsoft OneNote. For me, it is the killer app for my iPhone, iPad, iPod, Linux and Windows laptops. Well done Microsoft!…

