This is a very quick post – to point you in the direction of a short article I have written over at Smart Thinking.
How secure is your WordPress website and blog? Do you even know if your organisation’s website is built on WordPress?
I spend a lot of my time thinking and writing about cyber security (and the team would also add “drinking coffee”, and my answer is “but how do you do IT and cybersecurity without coffee?” – but back to my story) and one of the things I and the support team here at Octagon will always insist on is that a client activates multi-factor authentication, usually shortened to MFA, but see the notes below for other names.
The WordPress challenge
When you activate multi-factor authentication on your WordPress account, the WordPress mobile app does not work any more
When a client challenged our support team with this problem a couple of months back, they were very lucky, as we already had a cyber secure solution for the issue.
What is it?
Well it involves using multiple user accounts, but beyond that it is an IP of our WordPress service.
But this issue does illustrate a problem with multi-factor authentication, as it can easily interfere and in some cases stop the operations of your business. The answer is not the simple, “well switch it off”, what you need to create is a work around that allows the work to continue, but does not compromise the cyber security of your organisation.
Examine the risk
Let me start with a real world example:
At Octagon we manage the Microsoft 365 systems for many clients – we are the Global Administrators they all rely on for the smooth running of their 365 environments and the cyber security.
So obviously we have enabled MFA on every Administrator role. But this led us to a problem of accountability. The team members wanted a quick way to check when anyone was accessing a client site as an administrator – it is just good cyber security practice to be aware of what is going on, in real-time. As a team we put aside a morning to discuss the issue and try out several suggested solutions – we eventually found a workable solution, which we then implemented and wrote and added to our Cyber Security Plan. (We apply the same rule to our own Microsoft 365 set-up.)
What is it?
Well it would not be much of a cyber security step, if I published it in a blog for everyone to see. Even the clients do not know the details of this cyber security step, they just know we do it.
WordPress – Is your site secure and safe?
Let’s get back to my original question.
Is your WordPress site secure?
Many of you reading this will be using a web designer to look after your website. Have you ever asked them about the security (and back-up) they implement on your behalf? You should! You have a right to know.
Do they skip MFA, because it is difficult to implement with the sub-contractors they use in Exeter or Mumbai?
And if they say they do implement MFA for you, have you checked, has your cyber security consultant had eyes on the WordPress dashboard to verify this for you?
If you manage your own WordPress website you can implement, check and verify MFA across your user accounts. But do you have it correctly configured for the best cyber security and operational functionality?
Then there is the question, “Is the site backed-up correctly?”.
Sorry, there are lots of questions that you need to answer – or ignore – the choice is yours. But if you think a chat with someone, who understands cyber security and thinks about it a lot, and is experienced in finding secure work arounds for clients, would help? Well that’s why we are here.
Clive Catton MSc (Cyber Security) – by-line and other articles
Further Reading
Passwordlessness – Smart Thinking Solutions
Multi-factor authentication – the cyber security service with many names
Let’s start with what MFA is not. It is not a simple code set to you using text messaging. This is where things started, but we are beyond that now. MFA uses, for instance, an authenticator app on a smartphone or device (such as a Cisco fob), and a cryptographic algorithm, to give access to the service. This may be:
- A one time password that you then key in
- A hand-off through the app that allows you access
- A choice of options for you to pair with a number shown on the site you are trying to access
- Or something else that the security programmer has devised
Multi-factor authentication – MFA – is an essential step in any person’s or organisation’s cyber security – setting up a gateway between the threat actor and your account that only you have the key for. (There are issues with MFA, but we still need to use it – roll on passwordlessness.)
However for such a great cyber security tool, it has been complicated by historical inertia and a multiplicity of names. To help add some clarity for you through this fog, here is a short guide to various names for MFA.
- Dual-factor authentication (DFA) and Two-factor authentication (2FA) – this is where things started and can refer to the deprecated text message type service
- One Time Password (OTP) – this will come via the authenticator app
- Two-step verification
Amazon uses the second two terms for it’s multi-factor authentication. One word of warning, Amazon also offers you a check box for “Don’t require OTP on this browser”, only check this box for Amazon or any other MFA access, if you are absolutely sure, you are the only person who uses that machine or you completely trust anyone else who uses the machine. “Clive, Have you checked this box on your laptop?” I hear you ask. “No” is my answer, even though I am the only user of my laptop, and if I lend it to Diana, I trust her. Why would I fit a great lock on my house and then not always use it?
Here is how Microsoft approaches it:
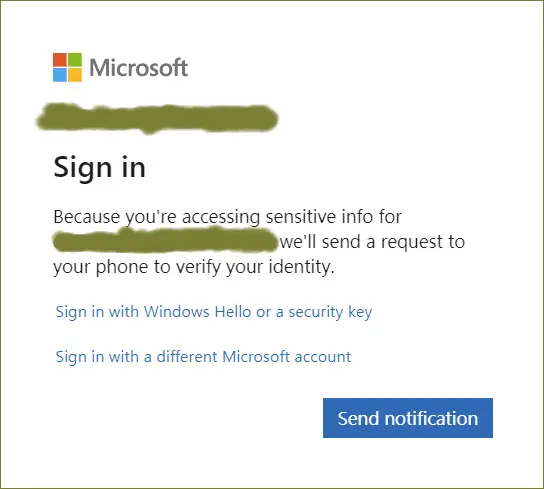
Not a mention of MFA etc anywhere, but the request will be sent to your authenticator app.
Authenticator apps
Finally a quick word on authenticator apps – only use one from a trusted company – our advice is either the Microsoft or Google authenticator app. Don’t worry you can use the Microsoft app to authenticate your Google account and you can use you Google authenticator to get access to your Microsoft account, so you do not need to install both (neither Microsoft or Google say that anywhere).